Scan code with SonarQube
Since QuickBuild 10, SonarQube, a continuous code inspection solution, can be added to your continuous integration workflow.
You can trigger SonarQube to analyze your source code by adding a step. The step can be:
- Sonar Scanner Step
- Maven Step
- Gradle Step
- Command line Step
Anonymous Group
As QuickBuild uses RESTful API to receive the results from Sonar server, a group named "anonymous" with RESTful API permission need be created first.
Configuring Webhook
QuickBuild uses Webhook to communicate with SonarQube. So firstly, you need config the webhook both in QuickBuild and in SonarQube.
QuickBuild Side
Go to configuration Settings page, then Webhook tab, you can define the SonarQube settings:
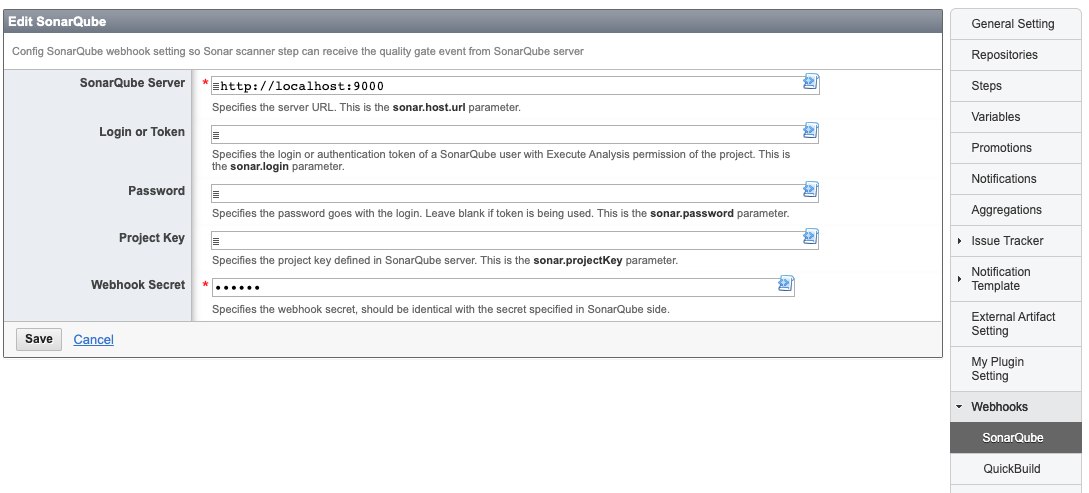
If the "Anyone" pseudo-group does not have permission to perform analyses, you'll need to
supply the credentials of a user with Execute Analysis permission for the analysis to run under. So, you need input Login or Token and Password for authentication. See more details at below page:
https://docs.sonarqube.org/latest/analysis/analysis-parameters/
Important
The Login or Token field and Password field are only used in Sonar Scanner Step. If you use
other steps. like Maven step or Gradle step, those fields are no use.
SonarQube Side
Go to project administration page, create a webhook:
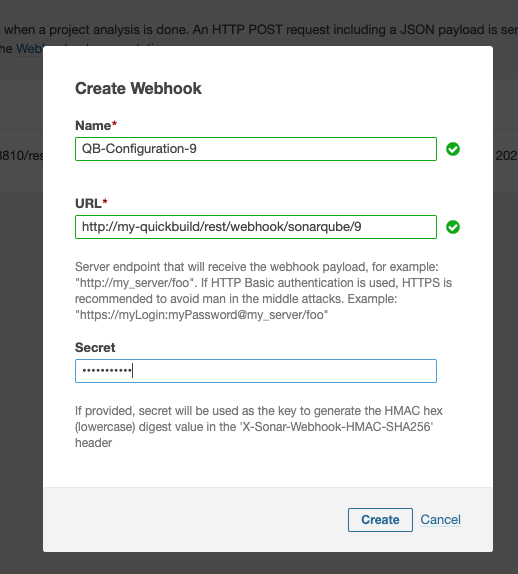
Please make sure the secret is identical to the secret filled in QuickBuild.
The URL is in below format:
http://{your-quickbuild-host}/rest/webhook/sonarqube/{configurationId}
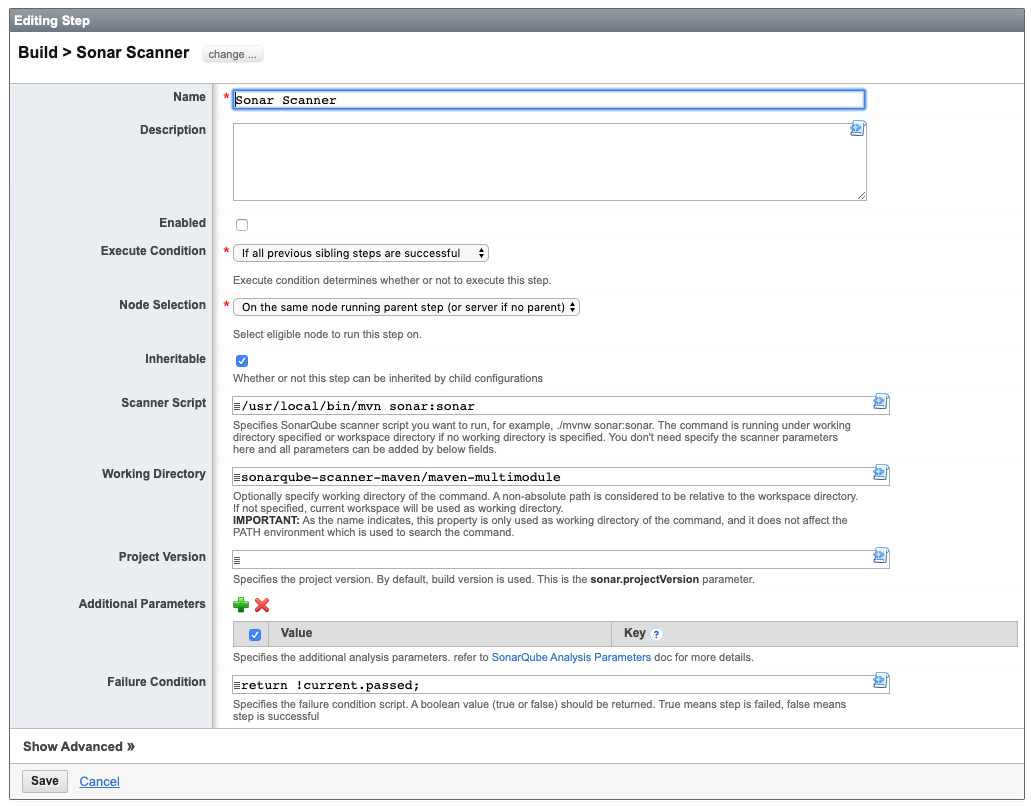
Sonar Scanner Step
In configuration workflow, add Sonar Scanner Step to trigger SonarQube to analyze your source code. And beside triggering the analysis, this step can also used to detect the quality gate result.
If you are using Maven Step or Gradle Step to run Sonar scanner, this step can only be used for detecting the quality gate only and fail the build if quality gate is not passed.
Maven Step
If you are using Maven step for triggering Sonar Scanner, you need add scanner parameters either in Maven properties section or in step build properties, see more details at below page:
https://docs.sonarqube.org/latest/analysis/scan/sonarscanner-for-maven/
The parameters can be found at below page:
https://docs.sonarqube.org/latest/analysis/analysis-parameters/
QuickBuild need one additional parameter in order to receive the webhook result: sonar.analysis.buildNumber:
sonar.analysis.buildNumber: ${build.id}
Property: sonar.analysis.buildNumber is required when using Maven Step to trigger the scanner, otherwise, there is no quality gate report.
Gradle Step
If you are using Gradle step for triggering Sonar Scanner, you need add scanner parameters either in Gradle properties file or in step build properties, see more details at below page:
https://docs.sonarqube.org/latest/analysis/scan/sonarscanner-for-gradle/
The parameters can be found at below page:
https://docs.sonarqube.org/latest/analysis/analysis-parameters/
QuickBuild need one additional parameter in order to receive the webhook result: sonar.analysis.buildNumber:
sonar.analysis.buildNumber: ${build.id}
Property: sonar.analysis.buildNumber is required when using Gradle Step to trigger the scanner, otherwise, there is no quality gate report.
Command line Step
If you are using command line step for triggering Sonar Scanner, you need add scanner parameters in command line directly:
https://docs.sonarqube.org/latest/analysis/scan/sonarscanner/
The parameters can be found at below page:
https://docs.sonarqube.org/latest/analysis/analysis-parameters/
QuickBuild need one additional parameter in order to receive the webhook result: sonar.analysis.buildNumber:
-Dsonar.analysis.buildNumber=${build.id}
Property: sonar.analysis.buildNumber is required when using command line Step to trigger the scanner, otherwise, there is no quality gate report.
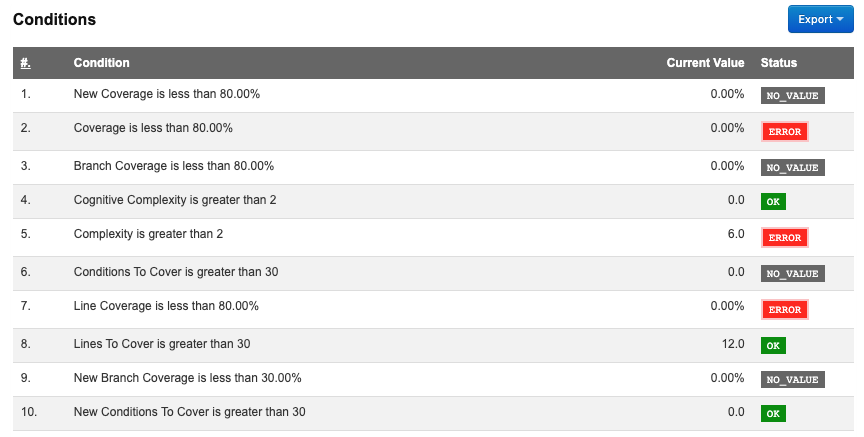
View Quality Gate Result
QuickBuild can receive the Quality Gate result from SonarQube webhook and showing them in build report tab: